My Journey into HTB Dante: Pivoting Through Pain, Earning the Glory
A beginner-friendly (and slightly painful) walkthrough of Hack The Box's Dante Pro Lab. Learn how I tackled pivoting, privilege escalation, and Active Directory challenges and what tools, tips, and scripts helped me survive and thrive in this intense red teaming lab environment.
“I thought I was just signing up for a lab. Turns out, I was enrolling in a virtual bootcamp that made me cry, learn, and finally… conquer.”
🧠 How It All Started
I first came across Dante while a friend was talking about his red teaming journey. He mentioned how Dante involved a combination of web, network, and Active Directory exploitation. As someone who has mostly focused on web security (the usual — XSS, SQLi, and some burp magic), this caught my interest.
I’ve done my fair share of HTB machines back in the early days — ah, those nostalgic times when registering on Hack The Box itself was a mini CTF (OGs know what I’m talking about 😎). Since Dante was described as a lab that blends various attack surfaces — and my friend mentioned that it required real pentesting skills — I decided to give it a try. Within 10 minutes, I had subscribed to the lab and was downloading the VPN connection pack.
💸 How to Access Dante Labs?
Dante is part of the Pro Labs section of Hack The Box. These are different from the regular HTB labs you access with a VIP or VIP+ subscription. The Pro Labs are much more realistic and are designed to simulate enterprise environments.
To access Dante, you’ll need to purchase a separate Pro Lab subscription, which costs around $49 USD/month (At least at the time I writing). Once subscribed, you also get access to other Pro Labs such as:
- Offshore
- Zephyr
- RastaLabs
- Cybernetics
- and more…
📝 Note: Pro Labs are not part of VIP or VIP+ plans. You need to buy this separately. I initially didn’t realise that and kept wondering why Dante wasn’t showing up on my dashboard.
Once subscribed, you’ll be provided with VPN access, and the lab starts functioning just like a real corporate network.
📚 What Does Dante Cover?
According to Hack The Box:
“This Pro Lab is aimed at information security beginners and junior pentesters. Dante features common vulnerabilities, misconfigurations, and attack paths seen in real engagements. It is an excellent opportunity for users to increase their knowledge in both Linux and Windows exploitation.”
From my experience, it does live up to this — but I personally feel that the exam was a little more challenging than “beginner-friendly”. So don’t expect a walk in the park.
Here’s what you’ll encounter:
- Windows and Linux privilege escalation
- Public exploits
- Web application attacks
- Lateral movement
- Buffer overflows (which I skillfully dodged because OSCP doesn’t require it anymore — but hey, knowledge is power!)
In total, Dante will help you flex your skills in:
1
2
3
4
5
🧾 Enumeration
💥 Exploit Development
🔄 Lateral Movement
📈 Privilege Escalation
🌐 Web App Attacks
So yes, if you are aiming for real-world internal pentest simulation, Dante will help you practice a wide variety of attack chains.
🏗️ Lab Structure
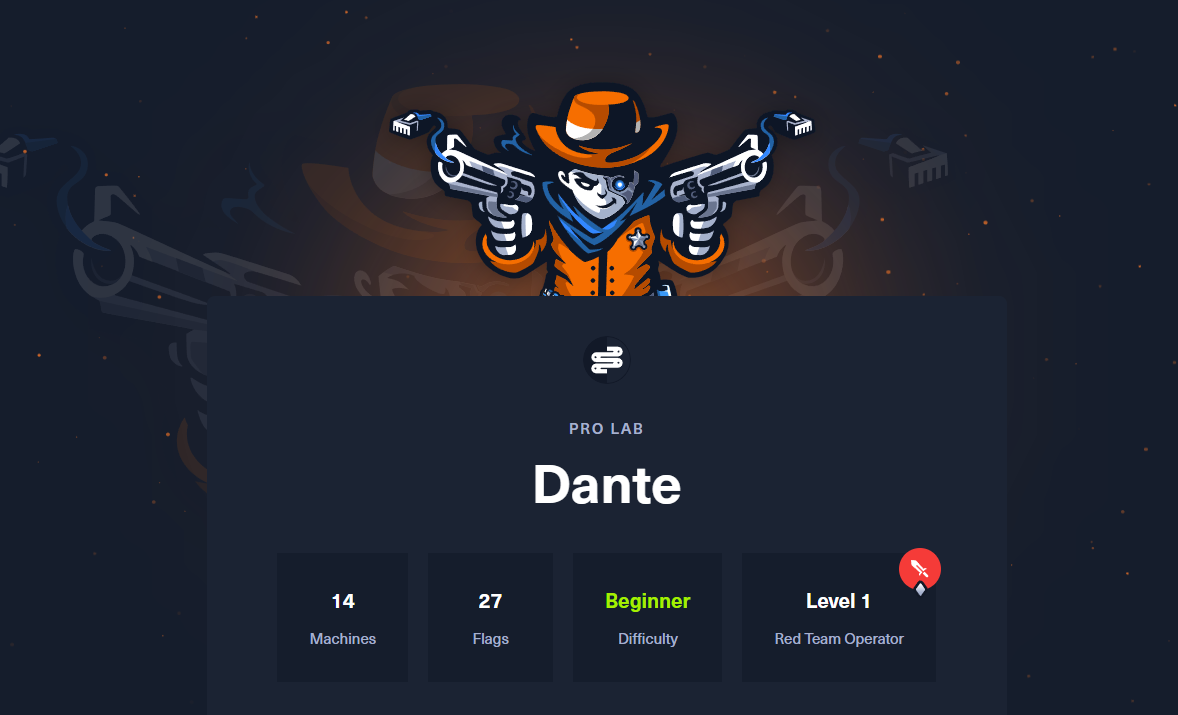
The lab contains 14 machines and a total of 27 flags. The flags follow the traditional DANTE{} format.
Well, don’t expect a well-connected corporate AD environment like RastaLabs. Surprisingly, there are very few interdependencies between machines. It felt more like several standalone HTB-style machines awkwardly joined into a network.
That said, the lab does simulate real-world attack paths well — if you enjoy the art of pivoting, you’re in for a treat. That said, pivoting and network movement are still essential — especially if you’re going after all the flags or planning to do the exam.
🧰 What You Should Be Ready With
Before jumping into Dante, I strongly suggest brushing up on the following skills and tools. These made my journey much smoother (after some initial struggle, of course).
🔁 Pivoting – The Main Character in Dante
This lab made me love and hate pivoting at the same time. You’ll have to chain multiple pivots — yes, double pivoting — to reach some of the juicy machines.
Tools to Master:
ssh -L,ssh -D(Basic tunnel spells)- Chisel – My go-to weapon
- Ligolo-ng – Pure magic!
sshuttle– Python-powered network ninjutsu
⚠️ Don’t skip pivoting practice — Dante will force-feed it to you anyway.
🧠 Tip: Keep a network diagram or a rough sketch to avoid confusion when dealing with multiple tunnels.
🗡️ NetExec: The Swiss Army Knife You Need
If you loved CrackMapExec, you’re going to adore NetExec. It’s the shiny successor, actively maintained, and pre-installed on Kali.
Perfect for:
- SMB, RDP, FTP enumeration
- Credential spraying
- Password reuse checks
- Getting a shell while sipping coffee ☕
Some of the ways I used it:
- To test login credentials across multiple IPs
- To enumerate SMB shares
- To spray passwords and check for reuse
1
netexec smb 172.16.x.0/24 -u usernames.txt -p passwords.txt --shares
Pro Tip: Use
--local-authand--sharesflags often!.
📜 WinPEAS & LinEnum
These privilege escalation scripts should be your default tools:
winPEAS.bat / winPEASx64.exe(for Windows)LinEnum.sh(for Linux)
They dig deep into the system so you don’t have to. Just remember — tools are only as useful as your ability to read their output.
Don’t just run them and scroll blindly — take time to understand what they’re reporting. Look out for:
- Misconfigured services
- SUID binaries
- Cron jobs
- Writable files/folders
- Token impersonation (on Windows)
👀 pspy – For Watching Background Activity
pspy is useful on Linux boxes where you don’t have root but want to see what background processes or cron jobs are running. Trust me this will help you a lot in the exam.
This tool helped me identify:
- When a root-level script was running
- If any user action was triggering something
- Misconfigured tasks that could be abused for privilege escalation
🐚 Be Ready With Shells
Make sure you have a good set of reverse shell payloads ready to use. Don’t spend time generating a new one every time.
Useful resources:
- https://revshells.com
- PayloadsAllTheThings
- My own resource site: https://infosecmania.com Shameless plug — submit your own tools too. Sharing is caring! ❤️
😬 Problems I Faced (and Solved)
Re-doing the initial lab again after a break was a nightmare. Every time I returned to the lab, I had to:
- Log into the first machine
- Set up Chisel or Ligolo again
- Reconfigure routes
It was time-consuming and frustrating.
Solution? I wrote a little script 💻 that:
- Uses discovered SSH creds to auto-login
- Sets up the
chiseltunnel - Gets you back where you left off — in seconds
Now, I just run this script and I’m ready to work.
SSH Errors from Misconfigured Files was an another issue while connecting between internal machines:
1
2
3
/etc/ssh/ssh_config: line 53: Bad configuration option: denyusers
/etc/ssh/ssh_config: line 54: Bad configuration option: permitrootlogin
/etc/ssh/ssh_config: terminating, 2 bad configuration options
This tripped me up hard. So I created a Python script that bypasses this and sets a clean SSH config.
You can find both these scripts on my github at Dante My Way
🧃 Final Tips Before You Dive In
Use Kali or Debian/Ubuntu for this lab. I tried to do it on my Mac (because, Apple fanboy vibes), but some exploits just refused to work. Save yourself the pain — run Kali inside UTM if you must.
Note every credential you find. You never know when they’ll come in handy.
Read flags carefully. Sometimes they hint at the next machine or pivot point.
Join the Discord server — the HTB community is awesome. They won’t spoon-feed you, but will give just the right nudge when you’re stuck.
Try unintended paths — creativity wins. If it works, it works.
🎉 Final Words
I won’t lie — Dante was tough, but extremely rewarding. The moment I saw the completion certificate, I felt an adrenaline rush , I always loved the way this certificate designed.
If you’re considering Dante, go for it. Not just for the certificate, but for the knowledge and confidence it gives. And hey, when you’re stuck in the middle of a painful pivot… just remember:
You’re not alone. You’re just in Dante’s Inferno. 🔥
Yes, you’ll get stuck. Yes, you’ll make mistakes. But that’s the point. You’ll come out of it much stronger and more confident.
Try harder when required. Try smarter whenever possible. And never stop learning.
Until next time, stay safe, stay sneaky, and may all your shells be stable — just remember to pivot before you panic!